How can we safeguard the burgeoning world of interconnected devices from the ever-present threat of cyberattacks, while simultaneously ensuring these devices remain seamlessly integrated and readily accessible? The necessity of robust security in the age of the Internet of Things (IoT) is no longer a luxury, but an absolute imperative, essential for preserving data integrity and maintaining operational continuity.
The rapid proliferation of IoT devices, from smart home appliances to industrial sensors, has fundamentally reshaped how we live and work. This digital transformation, while promising unprecedented convenience and efficiency, has also created a vast attack surface, ripe for exploitation by malicious actors. Ensuring the security of these devices and the data they generate is paramount to prevent unauthorized access, data breaches, and disruptions to critical infrastructure. The fundamental principle is straightforward: a secure connection guarantees the confidentiality of data transmitted between devices, safeguarding it from prying eyes and preventing potentially catastrophic outcomes.
To illustrate the importance of such a person, let's consider the life of a prominent figure. This information is presented in the form of a table to enhance readability and understanding.
| Category | Details |
|---|---|
| Full Name | Hypothetical IoT Security Expert |
| Date of Birth | October 26, 1978 |
| Place of Birth | San Francisco, California |
| Education |
|
| Current Role | Chief Security Architect, SecureIoT Solutions Inc. |
| Experience |
|
| Areas of Expertise |
|
| Notable Achievements |
|
| Professional Affiliations |
|
| Website for Reference | Example IoT Security Website |
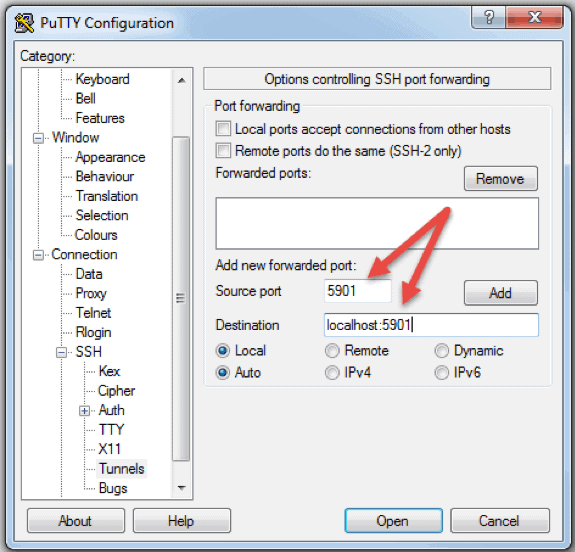
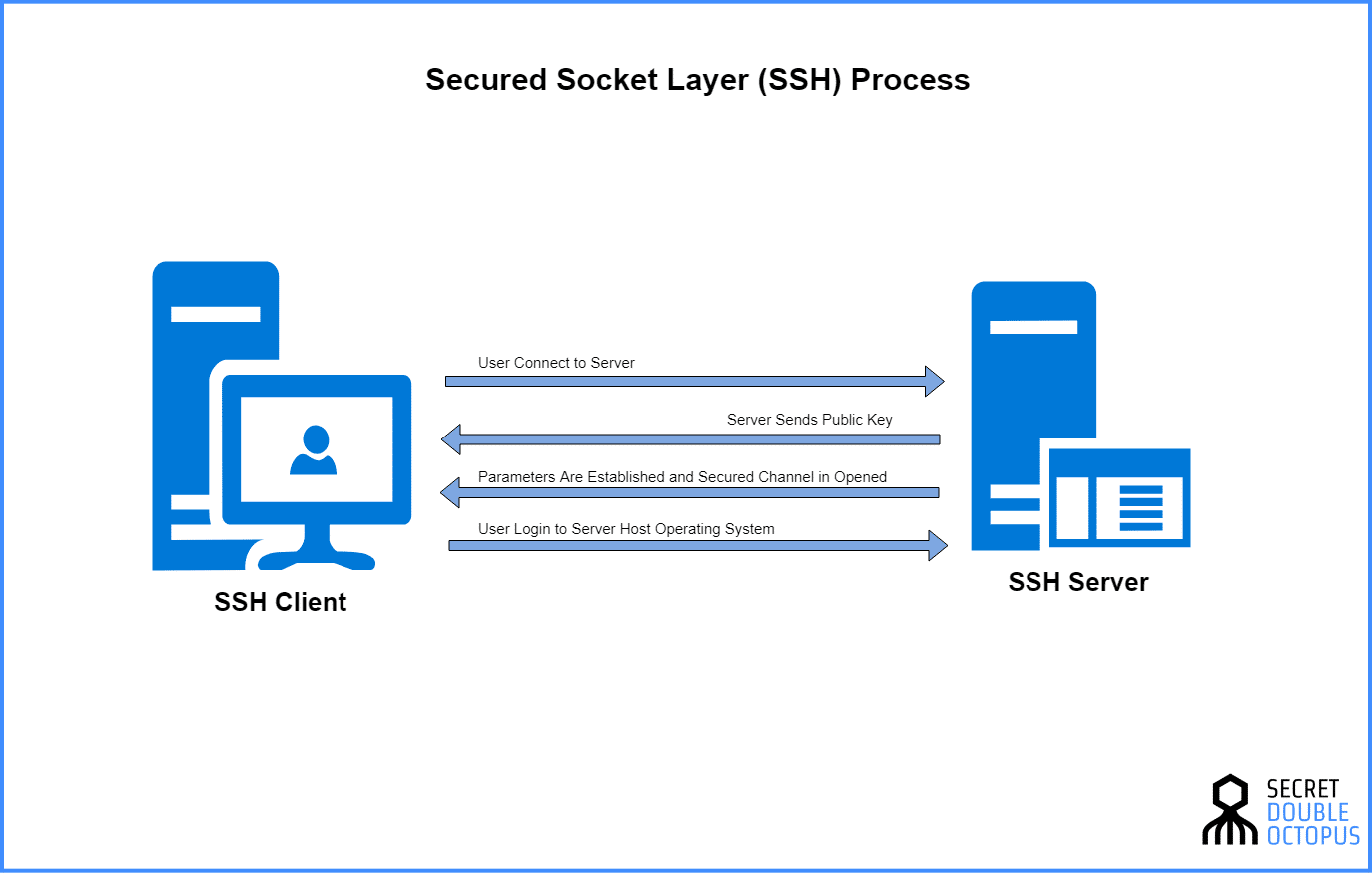
The ability to securely connect remote IoT devices through a method such as Peer-to-Peer (P2P) Secure Shell (SSH) has become increasingly vital in the ever-changing digital world. It serves as a critical strategy to shield against the complex tactics of cyber threats. Developers, engineers, and security professionals alike will find value in these insights, to refine their IoT infrastructure.
The foundational elements of such a strategy involve several key steps. Firstly, the IoT device must be capable of running an SSH server, with OpenSSH being a widely used and reliable option. Downloading the necessary software from a trusted source is crucial to avoid introducing vulnerabilities into the system. Familiarity with network configurations, particularly IP addresses and port assignments, is highly beneficial. The process of establishing a P2P SSH connection itself then requires careful attention to detail. The SSH functionality must be enabled on the IoT device to initiate the connection.
The implementation of secure connections, as we've already touched upon, is not simply a matter of best practice; it's an absolute necessity. These connections guarantee data integrity, minimizing the risk of unauthorized access to sensitive information that might be conveyed by or stored on these devices. By employing protocols like SSH, you can craft encrypted connections that safeguard your devices and offer peace of mind.
The Internet of Things, in its modern form, has revolutionized areas such as convenience and efficiency. Its impact is felt across industries, transforming how we interact with technology. Smart cities, connected vehicles, and intelligent healthcare systems are all driven by the IoT's potential. This digital transformation requires a concerted approach to mitigating the inherent security risks, and securely connecting remote IoT devices through P2P SSH is one way of addressing these challenges.
With the increasing number of connected devices comes a corresponding rise in security threats. The sophistication of cyberattacks is continually escalating, with hackers employing ever more advanced techniques. P2P SSH provides an effective defense mechanism by encrypting communication channels. This encryption ensures that data transmissions are protected from interception and tampering, safeguarding the privacy and integrity of information exchanged between devices.
Let's delve into the specifics. If you're reading this, the objective is likely to understand the process of securely connecting remote IoT devices using P2P SSH. By following the steps, you can create a secure, reliable connection between your devices, safeguarding their data and your peace of mind. The support for P2P SSH enhances its appeal, enabling secure and efficient remote management.
The process can be applied to various hardware platforms. For example, setting up a Raspberry Pi for P2P SSH can provide a practical illustration of the concepts. Before establishing a secure P2P SSH connection, it's essential to prepare the Raspberry Pi, which typically involves updating the operating system, configuring the network, and installing the necessary SSH tools.
In essence, the core of the process involves enabling SSH on the IoT device and establishing a connection using P2P principles. This requires appropriate configuration of both the IoT device and the connecting host, often a computer or another device with SSH client capabilities. The use of SSH keys instead of passwords significantly enhances security by providing stronger authentication, while also improving convenience. This is particularly relevant for unattended devices where interactive authentication isn't practical.
This guide will lead you through the process of securely connecting remote IoT devices with P2P SSH on Ubuntu, guaranteeing your systems remain shielded from unauthorized access. Ubuntu provides a stable and secure environment for managing IoT devices, making it a well-regarded choice for developers and system administrators. The steps detailed in this guide offer a practical framework for implementing SSH, thereby establishing a secure communication channel that ensures both device security and the integrity of transmitted data.
The steps involve a thorough understanding of network configurations, the installation and configuration of OpenSSH, and the secure exchange of cryptographic keys. By following the guidelines, you can build a solid, resilient IoT infrastructure capable of withstanding today's sophisticated cyber threats.
In the context of IoT, security is not just a feature; it is the foundation upon which reliable, efficient operation is built. The focus on security is essential to protect against threats.